Author Archives: David Lineman
Information Security Policy: The Complete Guide
Complete Guide to Information Security Policy: Success in policy development and deployment In today’s digital [...]
Aug
New Acceptable Use of AI Training
Houston, Texas – Information Shield today announced the release of new Security Awareness Training for [...]
Jul
Top Information Security Policies to Protect Your Business in 2025
Introduction to Information Security Policies In today’s digital world, data is one of the most [...]
Jun
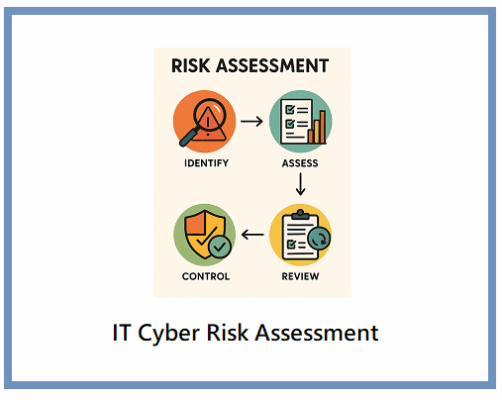
Ultimate Guide to Cyber Risk Assessment: Tips & Tools (2025)
Cyber risk assessment isn’t just for large enterprises. Small and medium businesses, non-profits, and even [...]
May
Are you doing a real Cyber Security Risk Assessment?
A Cyber Risk Assessment is required in most cyber security frameworks and regulations. Is your [...]
Apr
5 Steps to Simplify DORA Compliance
Streamline Compliance with the Digital Operational Resilience Act (DORA). Save thousands building and documenting a [...]
Feb
Streamline DORA Compliance
Streamline Compliance with the Digital Operational Resilience Act (DORA). Save thousands building and documenting a [...]
Jan
3 Ways to Validate your Cyber Security Program
If you are handling sensitive data in your business, sooner or later you will be [...]
Dec
Information Security Policies: Address Regulatory Requirements
Management often struggles to justify the expense of developing and maintaining written information security policies. [...]
Nov
5 Elements of Effective Information Security Policies
Information Security Policies – The Foundation Information Security Policies are the foundation of your cyber [...]
Oct