Streamline Cyber Security Compliance
Define, Deliver and Demonstrate a robust Information Security Program in one platform
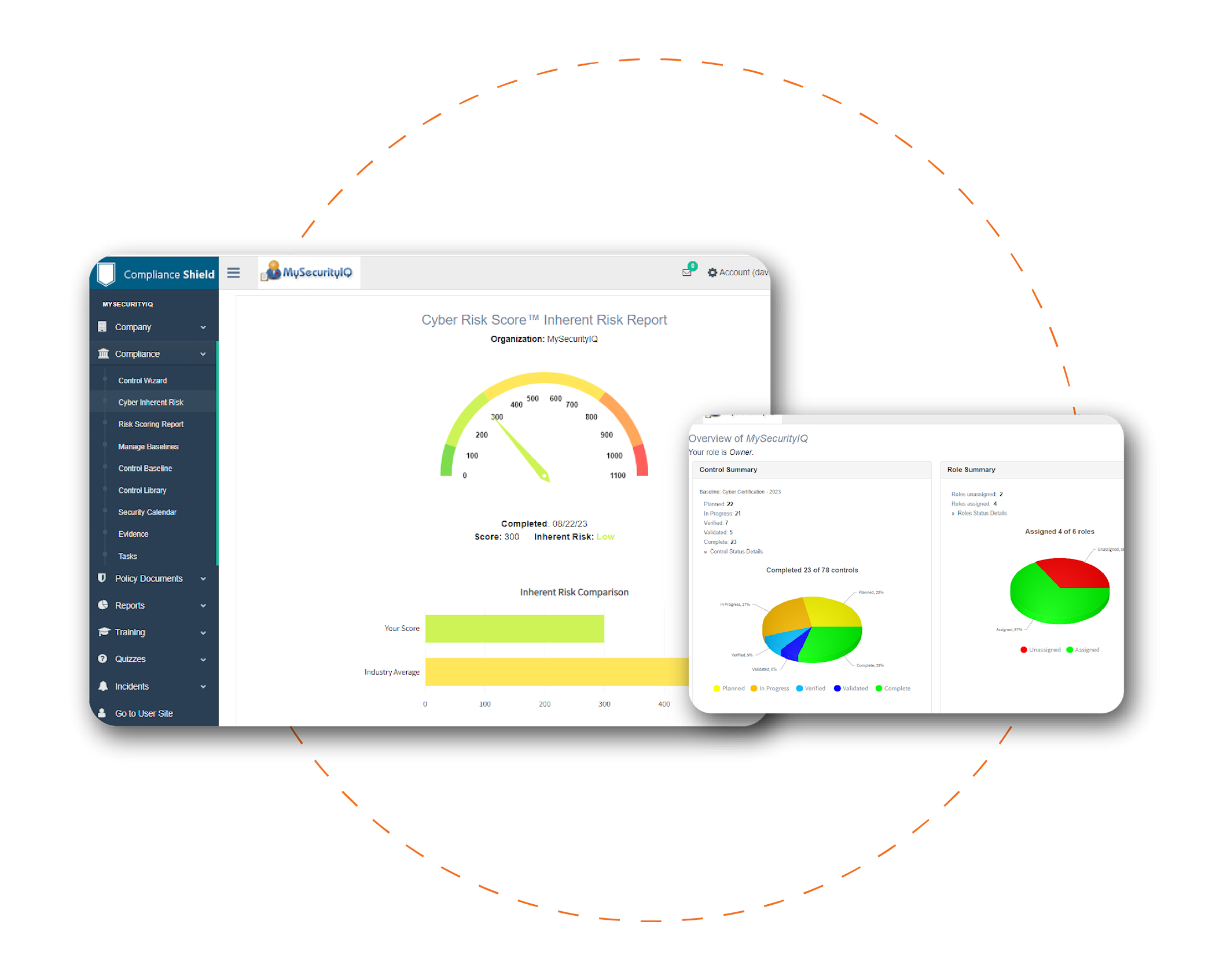
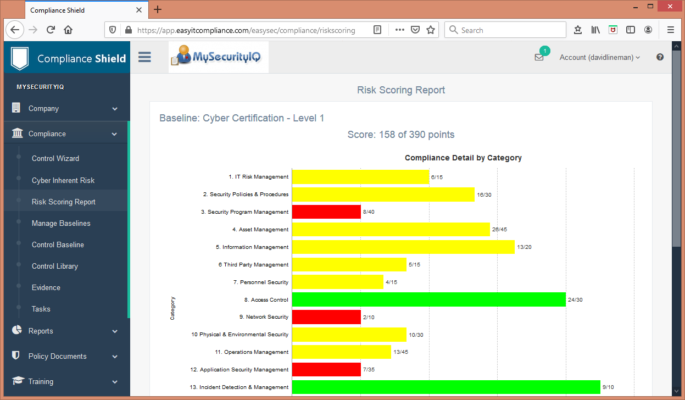
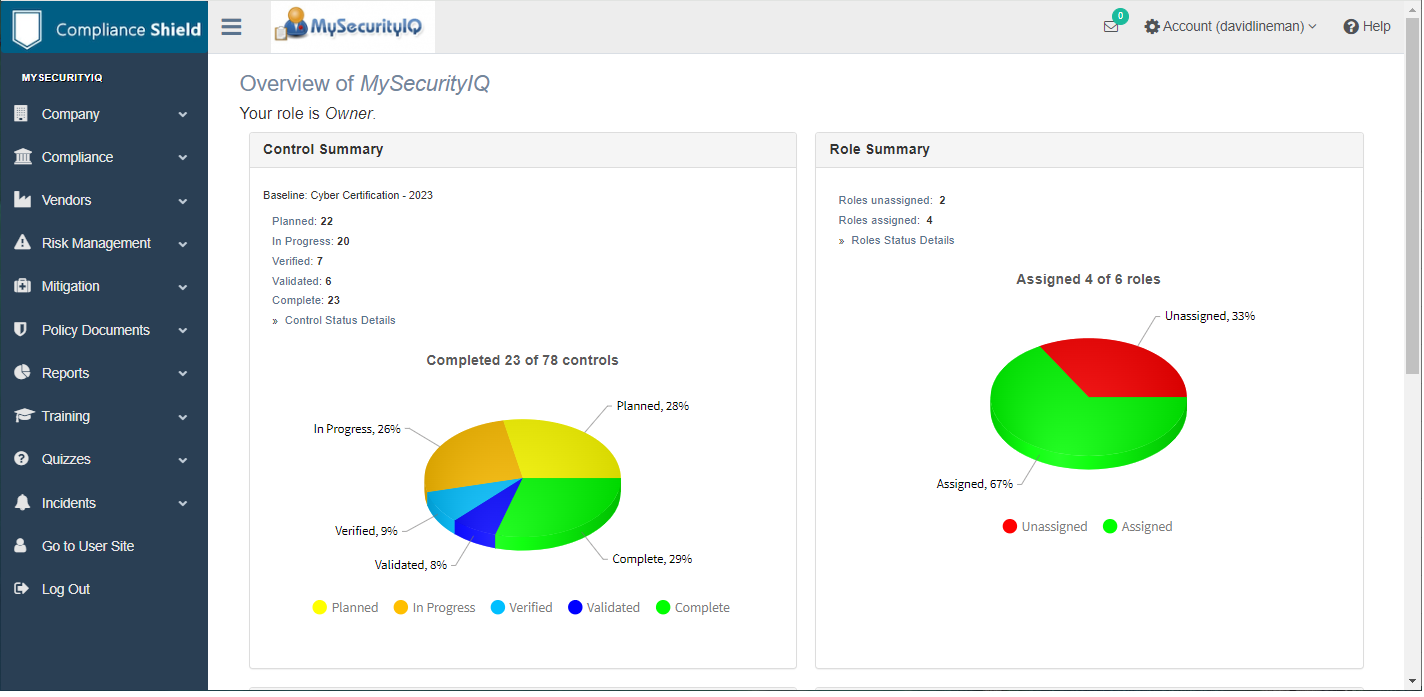
Why spend weeks of time and thousands of dollars on consultants when you can use ComplianceShield? We have streamlined the cyber compliance process by combining our world-recognized policy compliance library with an easy-to-use software platform.
Build a robust, defensible cyber security program in minutes with our Compliance Wizard and pre-build Baselines for ISO 27002, NIST CSF, CMMC, HIPAA, SEC and many others. Loaded with policy templates and compliance tools, ComplianceShield saves thousands of dollars and months of manual effort.