Save Time and Money Building a Defensible Cyber Security Program
If you are in business today, you need to demonstrate to customers, business partners and regulators that your organization is “cyber secure.” But what does that mean? How do I know what it means to be “cyber secure” and how can I measure my progress and know when I am done? Information Shield can help your organization save thousands of dollars and hundreds of hours building a defensive program.
Develop Information Security Policies Quickly
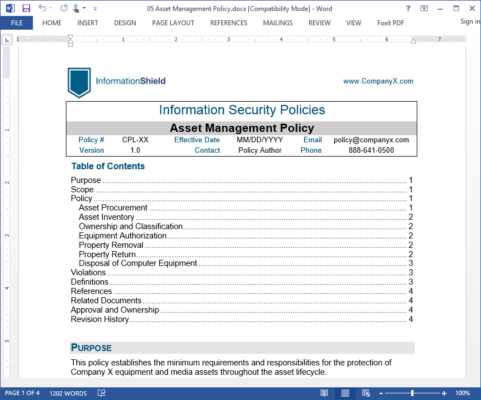
An information security program only exists in the eyes of regulators or auditors if it is supported by a comprehensive set of written information security policies and procedures. Use our world-leading policy template library to quickly develop policies covering essential information security and data privacy topics. Information Security Policies Made Easy (ISPME) is the “Gold Standard” library of pre-written information security policies used by over 10,000 organizations and recommended by security pros.
- Over 40 essential sample security policy templates in MS-Word format, covering topics from Network Security to Passwords.
- Security policy maps to key regulations such as ISO 27002, HIPAA, NIST CSF, PCI-DSS and others.
- Policy Statement Library of over 1600 information security policies and expert commentary covering our Common Policy Library.
- Expert Policy Advice on how to effectively organize and implement a security policy project in your enterprise.
- Time Saving Forms and Procedures to help maintain your information security policy program, including Policy Compliance Agreement, Policy Exception Request, and Incident Reporting Form.
Document the Cyber Security Organization
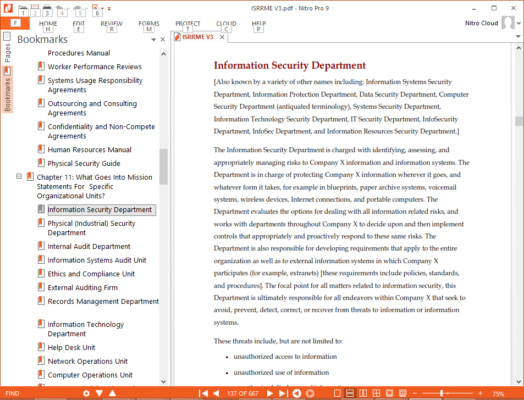 A defensible cyber security program also requires that the Information Security Organization is properly defined and documented. Management accountability must be established for proper cyber governance. Our library of Information Security Roles and Responsibilities can be used to quickly define the security requirements of key job roles and departments.
A defensible cyber security program also requires that the Information Security Organization is properly defined and documented. Management accountability must be established for proper cyber governance. Our library of Information Security Roles and Responsibilities can be used to quickly define the security requirements of key job roles and departments.
- Over 40 pre-written information security related job descriptions.
- Over Department Mission Statements
- Security Organization Templates
- Expert Advice on how to effectively build, document, and support an information security organization.
Automate Your Cyber Security Program
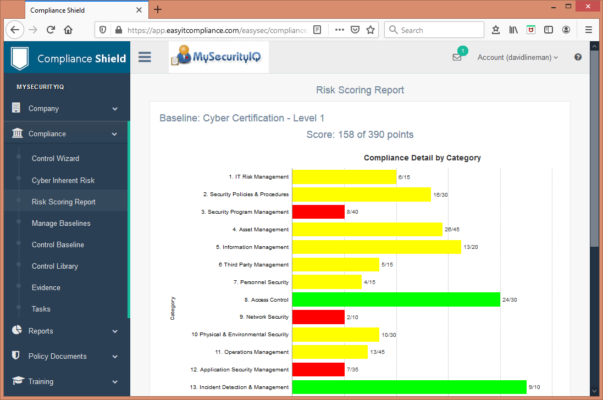 Our “all in one” cyber solution, ComplianceShield™ combines our Security Policy Content with a suite of simple, integrated security management tools that allow you to build, document and track your information security program. Use our Compliance Wizard to build a cyber security framework in minutes and then track and measure your progress. Our Cyber Risk Scoring enables easily bench-marking with other organizations. Our platform helps automate external audits such as SOC II reports and our own Information Shield (TM) Cyber Security Certification. Key features include:
Our “all in one” cyber solution, ComplianceShield™ combines our Security Policy Content with a suite of simple, integrated security management tools that allow you to build, document and track your information security program. Use our Compliance Wizard to build a cyber security framework in minutes and then track and measure your progress. Our Cyber Risk Scoring enables easily bench-marking with other organizations. Our platform helps automate external audits such as SOC II reports and our own Information Shield (TM) Cyber Security Certification. Key features include:
- Complete Sample Policy Library – Includes all of our 40+ Security Policies Made Easy sample documents. all mapped to our Common Policy Library (CPL)
- CPL Control Library – Over 300 information security controls to help define and document your information security program. Each control contains essential elements including sample policy text, example evidence and assessment questions.
- Compliance Program Tracking – Easily establish an information security control baseline and track progress for each element of your program. Generate compliance reports giving management a simple snap-shot of your entire program.
- Educate and Train Employees – Train users on essential information security principles using our built-in security awareness training library.
- Distribute and Track Policy Awareness – Quickly publish policy and procedure documents to users, verifying acknowledgment and understanding.
- Security Incident Reporting – ComplianceShield enables users to report security incidents which are then managed and tracked by the compliance staff.
Get Expert Help
![]() If you don’t have the time or experience to develop and support your cyber security program, Information Shield Professional Services can do the work for you. By leveraging our existing library of pre-written policies, our staff of experts can deliver a customized, comprehensive set of written policies, standards and procedures at a fraction of the cost of most consultants. If you need ongoing support but don’t have the budget to hire a full-time security officer, let one of our team become your Virtual CSO with a convenient monthly subscription.
If you don’t have the time or experience to develop and support your cyber security program, Information Shield Professional Services can do the work for you. By leveraging our existing library of pre-written policies, our staff of experts can deliver a customized, comprehensive set of written policies, standards and procedures at a fraction of the cost of most consultants. If you need ongoing support but don’t have the budget to hire a full-time security officer, let one of our team become your Virtual CSO with a convenient monthly subscription.
