Simplify NSCC Cyber Security Confirmation
The financial services industry has created a new level of accountability for cyber security programs. The National Securities Clearing Corporation (NSCC) filed with the SEC a Proposed Rule Change to Require Confirmation of a Cybersecurity Program. The Confirmation is a formal declaration by senior management that an organization has implemented a cyber security program that addresses common security frameworks.
The Challenge: Developing a Defensible Cyber Security Program that can be tracked and verified
In order for an organization to “Confirm” its cyber readiness, an organization must first develop, document and then deliver a robust set of information security controls that address key areas of cyber security risk. According to the NSCC cyber program, this framework must map to one or more leading cyber frameworks including NIST CSF or ISO 27002. Once adopted, the organization must validate the implementation and effectiveness of these controls with internal and external audits.
The Solution: Simplified Cyber Security ComplianceShield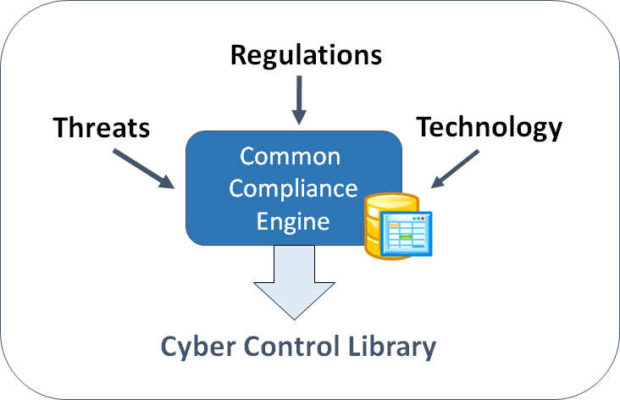
Using our Three Step Compliance Process, organizations can use our ComplianceShield platform to dramatically streamline the process of defining, documenting and demonstrating compliance with a robust cyber security program. No longer do you have to spend thousands of dollars on consultants just to figure out where to begin. Using our Compliance Wizard you can get started in minutes and save hundreds of man-hours defining, documenting and then validating a robust cyber security program.
Key Features to Streamline NSCC Compliance
Define a Cyber Security Control Framework
Build a robust Information Security Program in minutes using our Compliance Wizard and built-in Baseline Templates. All of our controls are mapped to leading frameworks including ISO 27002, NIST-CSF, HIPAA and many others. Track the assignment and completion of essential program elements.
Quickly Develop Security Policies – Common Policy Library (CPL)
Save time and money developing security policies with over 40 pre-written information security policy templates. Our unique Common Policy Library (CPL) has over 300 controls addressing the latest technologies, threats and regulatory requirements. Easily create policies to comply with ISO 27002, HIPAA, NIST-CSF, PCI-DSS and more.
Establish Management Accountability
ComplianceShield enables the organization to quickly document accountability for various program elements based on standardized security job functions. Our library of pre-defined information security job descriptions helps save many hours documenting the information security organization.
Streamline Compliance Audits
Organizations can easily measure and track compliance of the cyber security program using simple management reports. Tie compliance evidence and artifacts directly to controls and store all of the audit information in one secure central repository.
Measure and Benchmark with Cyber Risk Scoring™
Easily track the implementation of each critical information security control using our Cyber Maturity Risk Scoring. Risk Scoring Reports provide a simple overview of your entire information security program.
Manage, Distribute and Track User Awareness of Policies
Automatically distribute policies, procedures and training directly to users based on their role within the organization. Verify user understanding by tying assessments to specific policies. Track results for each user, enabling management to quickly determine who is in compliance with requirements to read and acknowledge policies.
Report and Manage Security Incidents
Flexible Incident Reporting helps track and manage details of information security incidents, including what was affected, incident categorization, severity, date and time of detection, declaration disclosure and resolution.
Demonstrate “Due Diligence” to Regulators and Insurance Providers
Quickly demonstrate cyber security due-diligence to senior management, auditors, customers and insurers with a few simple reports. Manage and store evidence of control status for easy audit.
Get Started Today! (It takes less than 5 minutes)
Contact us today for a Free 30 Minute Consultation on how your organization can streamline and demonstrate cyber security compliance. Or register for a FREE 14 Day Trial of ComplianceShield.
Learn More Contact Us
Key Cyber Security Requirements of the NSCC
The key requirement of the new law is that Management will be held accountable for cyber security by requiring a formal attestation.
The Confirmation Form is an electronic form that your designated Senior Executive / Control Officer must complete and sign to confirm that your organization has a resilient cybersecurity program that is aligned to an established framework thus protected against cyber-attacks.
According to the DTCC – the following elements are required for a program confirmation:
What are the Elements of a Confirmation Form?
- A comprehensive cybersecurity program
- Cybersecurity policies and procedures approved by senior management or the company’s board of directors
- Alignment with industry standard best practices and guidelines
- A program to review the risks of third parties used to connect to DTCC
- A process to remediate cyber issues identified to fulfill regulatory and/or statutory requirements
- Periodic update of cybersecurity program and framework
- A comprehensive review of the cybersecurity program and framework has been conducted by one of the following:
- The Company, which has filed and maintains a current Certification of Compliance with the Superintendent of the New York State Department of Financial Services (NYSDFS) pursuant to 23 NYCRR 500
- A regulator who assesses the program against a designated cybersecurity framework or industry standard (OCC: Office of the Comptroller and the FFIEC CAT)
- An independent external entity with cybersecurity domain expertise (SOC2 Certification, ISO 27001 Certification, NIST CSF assessment)
- An independent internal audit function reporting directly to the board of directors or designated board of directors committee of The Company, such that the findings of that review are shared with these governance bodies
The Information Shield Solution
Our cyber security products help address all of these key requirements. Contact us today to learn how to streamline compliance.
