Demonstrate cyber security to customers, regulators and insurance providers.
If you are in business, you will be asked to demonstrate that you have a robust cyber security program in place.
Forget the expensive consultants and complex software systems that take weeks to deploy! ComplianceShield enables your organization to develop a security program in minutes!
See Bob’s Compliance Journey with ComplianceShield
The “Made Easy” Compliance Solution
Information Shield has taken our “Made Easy” security policy library to the next level with ComplianceShield. ComplianceShield helps automate all aspects of cyber security governance. Pre-loaded with Control Baselines (ISO 27001, CSF, HIPAA. FTC. CMMC) and Security Policy Templates, it has everything you need in one integrated platform.
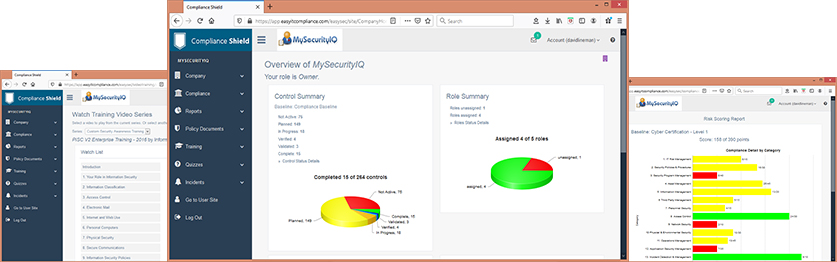
Pre-Built Cyber Security Control Baselines

Key ComplianceShield Features Compliance Automation
Use our Common Control Library (CCL) to quickly build a cyber security program to comply with all common regulations and frameworks,
Develop Information Security Policies
Create security policies in minute with our ISO 27002 policy template library. Over 50 policies, procedures and plans than can easily be customized.
Measure and Track User Acknowledgement
Customized “User Portal” enables you to easily distribute security policies, training and assessments to employees and contractors. Validate user understanding and formal acknowledgement of security policies.
Assess and Manage Third Party Vendors
ComplianceShield supports a complete Vendor Risk Management process using our Common Vendor Assessments. Easily create and distribute Cyber Risk Assessments to vendors and track results.
Educate and Train Users
Educate users with built-in security awareness training. Customized “User Portal” enables you to easily distribute policies and training to employees and contractors.
Measure and Track Control Compliance
Measure and track compliance with Controls including evidence storage and sharing. Easily show management progress against compliance goals.
Manage Information Security Incidents
Report, track and manage information security incidents. Multiple custom incident types and routing to response teams. Supports built-in Incident Response Procedure.
Perform IT Risk Assessments
Educate users with built-in security awareness training. Customized “User Portal” enables you to easily distribute policies and training to employees and contractors.
Define the Information Security Organization
Measure and track compliance with Controls including evidence storage and sharing. Easily show management progress against compliance goals.
Manage Ongoing Compliance
Report, track and manage information security incidents. Multiple custom incident types and routing to response teams. Supports built-in Incident Response Procedure.
Have questions about building a cyber program that works?
Call us now for a FREE 30 minute phone consultation with a cyber expert. 888-641-0500

Trusted by Organizations Around the World
We have helped hundreds of companies develop the security policies and programs they need to address cyber laws and pass third-party audits






“Information Shield has enabled us to simplify compliance for our portfolio companies and save thousands on program development”
Jason Taule, CISO Maryland Innovation Center

“Thanks to the folks at Information Shield, we have been able to quickly build our program and pass our vendor assessment requirements!”
Rich Bartoli, VP BEI Systems
