Transform your vendor risk assessment by actually helping your vendors pass!
The Vendor Risk Management Challenge
Performing vendor due-diligence across hundreds or even thousands of vendors can consume a large amount of resources for already strapped risk management teams. Today’s solutions typically involve sending large spreadsheets that are difficult to manage and even harder to answer. This process is very slow and expensive, producing inconsistent results.
The ComplianceShield Solution
Transform your vendor risk management program into a consistent, risk-based portfolio management tool while saving hundreds of hours. Using ComplianceShield, organizations can replace their existing process with an automated platform that achieves better, faster answers to risk assessment questions. Benefits of using ComplianceShield for vendor portfolio management:
- Simple – A single email enables your vendors to self-register in the system within minutes. No software to install and no professional services.
- Consistent – Vendors input results and evidence in a single, consistent format that works across hundreds or thousands of vendors. The CPL Risk Score creates a measurable baseline of security maturity.
- Measurable – Our Cyber Risk Score provides an objective view of the cyber maturity of each vendor. Quickly determine which vendors present the greatest risk and focus on remediation plans.
- Better – Rather than building your own assessments, organizations select from a library of best-practice security baselines, allowing different vendors to receive different assessments based on their true risk profile.
- Fast – Vendors can establish a security program and begin providing evidence in minutes instead of weeks.
- Secure – Vendors evidence is stored in a secure central repository. Confidential information is no longer sent via email chains.
- Continuous – Organizations have a single dashboard where they can view the status of all vendors in real-time. Organizations can easily focus effort on vendors that need the most help.
Learn more or request a demo and free consultation.
Watch Jane’s story: Simplify Vendor Security Assessments (90 sec video)
ComplianceShield streamlines the entire vendor risk management process. Easily measure Cyber Risk Scores across your entire vendor population.
Try our FREE TRIAL. It takes less than 5 minutes to get started.
Key ComplianceShield Features for Automating Vendor Assessments
Quickly Load and Assign Vendors
Create and update your vendor inventory by loading or inviting vendors to the ComplianceShield platform. Vendor Profiles allow you quickly assign vendor risk profiles and matching assessments.
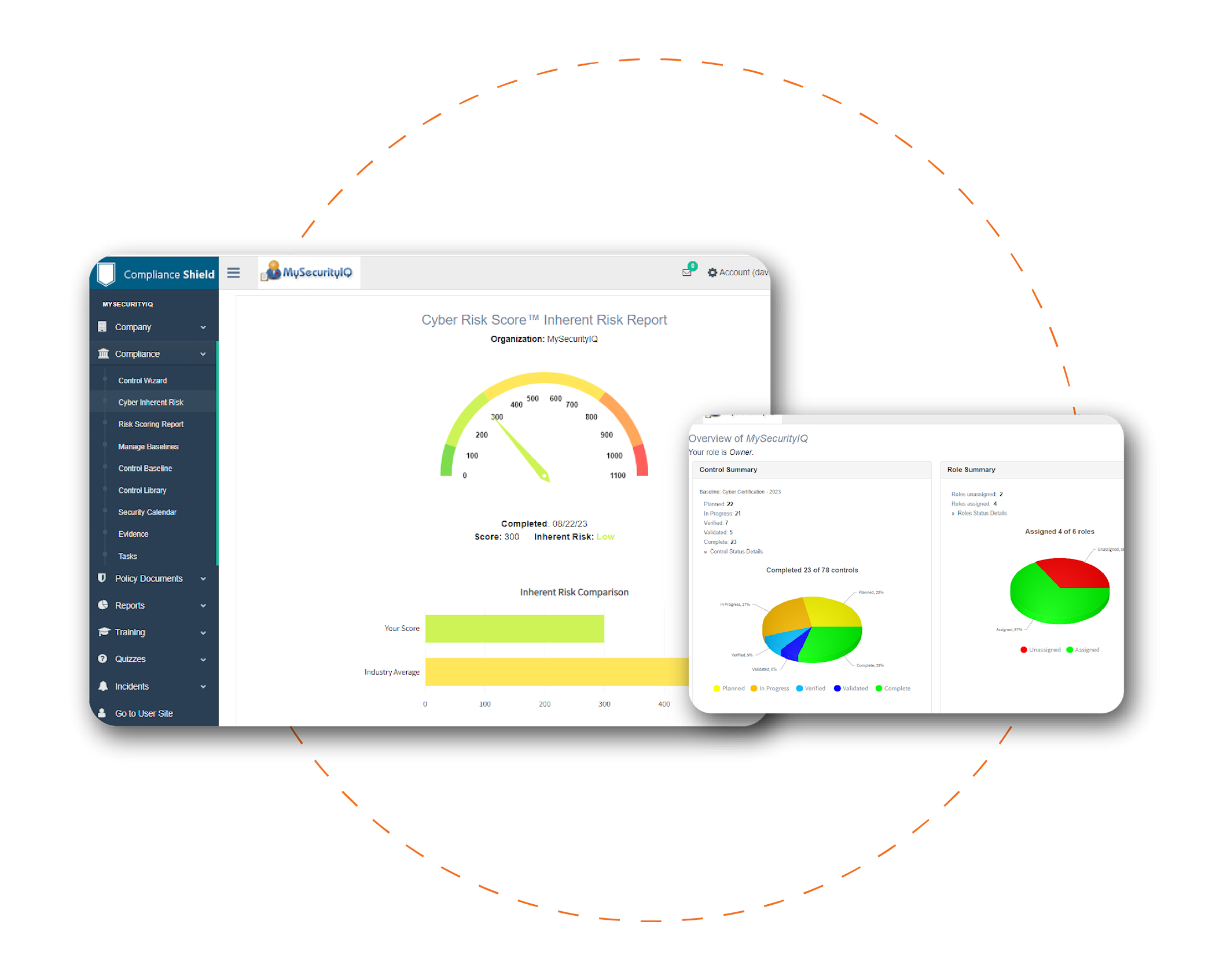
Measure Vendor Inherent Cyber Risk Score
Use our Cyber Risk Score assessment to quickly assess the inherent risk of vendors. Inherent Risk helps determine what level of assessment is required to best match vendor risk profiles to assessments
Build Vendor Cyber Assessments
Save time using our Common Vendor Assessments, a Library of pre-built assessment questions designed to understand and measure cyber risk and maturity of vendors.
Automate Vendor Assessments
No more speadsheets! Use our Vendor Management workflow to automatically distribute vendor assessments to each vendor based on their risk profile. Collect, store and review evidence of compliance.
Measure and
Track Vendor Compliance
Easily view the information security posture of your entire vendor organization in a single compliance dashboard. Validate and benchmark vendor compliance programs by using our Cyber Risk Score report. Drill down into specific questions and responses with ease.
Manage Vendor Information Security
Incidents
Once registered with ComplianceShield, vendors can report incidents directly to your team with a secure portal. Incident response plans and procedures can help the vendor more effectively respond and contain events.
Measure and Track
Vendor Policy Acknowledgement
Automatically distribute policies, procedures and training directly to vendors based on their cyber risk and relationship. Require vendors to read and formally acknowledge the Security Policies that apply to them.
Get Expert Help
Use our team of cyber experts to navigate the entire process. Let us act as your virtual CSO and help you clarify and respond to questions with professional answers that help pass the assessment. If you wish, our team can stay on for periodic updates.
Document the Vendor Risk Assessment Program
Use our built-in security policy template library to quickly build a Vendor Risk Management Policy and procedures. Automatically tie the vendor risk process to common controls and regulatory requirements.
