Security Policy Whitepapers
Information Security Policies: Address Regulatory Requirements
Management often struggles to justify the expense of developing and maintaining written information security policies. In the following table we show various regulatory frameworks that explicitly or implicitly require written information security policies.
Security Policies: Requirements Regulatory Map
| Regulation/Framework | Industry/Region | Policy Requirement |
| Payment Card Industry Data Security Standard PCI-DSS | Credit Card Processing | Requirement 12: Maintain a policy that addresses information security |
| ISO/IEC 27002:2022 Section 5.1 Information Security Policy Document | Security Management Framework (International) | A written policy document should be available to all employees responsible for information security. |
| HIPAA (Health Insurance Portability and Accountability Act of 1996) – HiTECH Security Final Rule | Healthcare (U.S.) | Policies and Procedures 164.316 (a) (R) Implement reasonable and appropriate policies and procedures to comply with the standards, implementation specifications, or other requirements of this subpart. |
| US-CSF V2.0 – Cyber Security Framework Governance (GV) | US – All Sectors | ID.GV-1: Organizational information security policy |
| FFIEC IT Examination Security Handbook – Policies and Procedures | US – Financial Services | “The board should approve written information security policies and the written report on the effectiveness of the information security program at least annually.” |
| FTC Safeguards Rule – 16 CFR Part 314 | All Companies (U.S) | Develop written information security policies (5) |
| SIG – BITS Standard Information Gathering Questionnaire (v6.0) | Banking – Vendor Assessment | SL.23 – Is there an information security policy that has been approved by management, communicated to appropriate constituents and an owner to maintain and review the policy? |
| DORA is the Digital Operational Resilience Act | EU Financial Sector and Vendors | Financial Entities must document key controls with written policies. |
| Gramm-Leach-Bliley Act (GLBA) Title V – Section 501 Interagency Guidelines Establishing Standards For Safeguarding Customer Information | Financial Services (U.S.) | “Each Bank shall implement a comprehensive written information security program [policies] that includes administrative, technical and physical safeguards.” |
| NERC CIP – Cyber Security Standard CIP-003 Security Management Controls | Energy/Infrastructure (U.S.) | Requirement 1. The Responsible Entity shall create and maintain a cyber security policy that addresses the requirements of this standard and the governance of the cyber security controls. |
| Federal Information Security Management Act (FISMA) NIST SP 800-53 | Federal Government (U.S.) | “(a) The head of each [Federal] agency shall delegate to the agency Chief Information Officer ensuring that the agency effectively implements and maintains information security policies, procedures, and control techniques;” |
| PIPEDA (Bill C6) – Personal Information Protection and Electronic Document Act | All Industries (Canada) | 4.1 Principle 1 – Accountability Organizations shall implement policies and practices to give effect to the principles. |
| GDPR – General Data Protection Regulation | All Industries (European Union) – Data Privacy | Organizations must “implement appropriate technical and organizational measures to protect personal data.” |
| NYS-DFS – 23 NYCRR Part 500 | Security Framework / Insurance | Develop and Maintain Written Information Security Policies (500.03) |
Table 1: Cyber Security Laws and Frameworks
Cyber Regulatory Summary – The need for policy
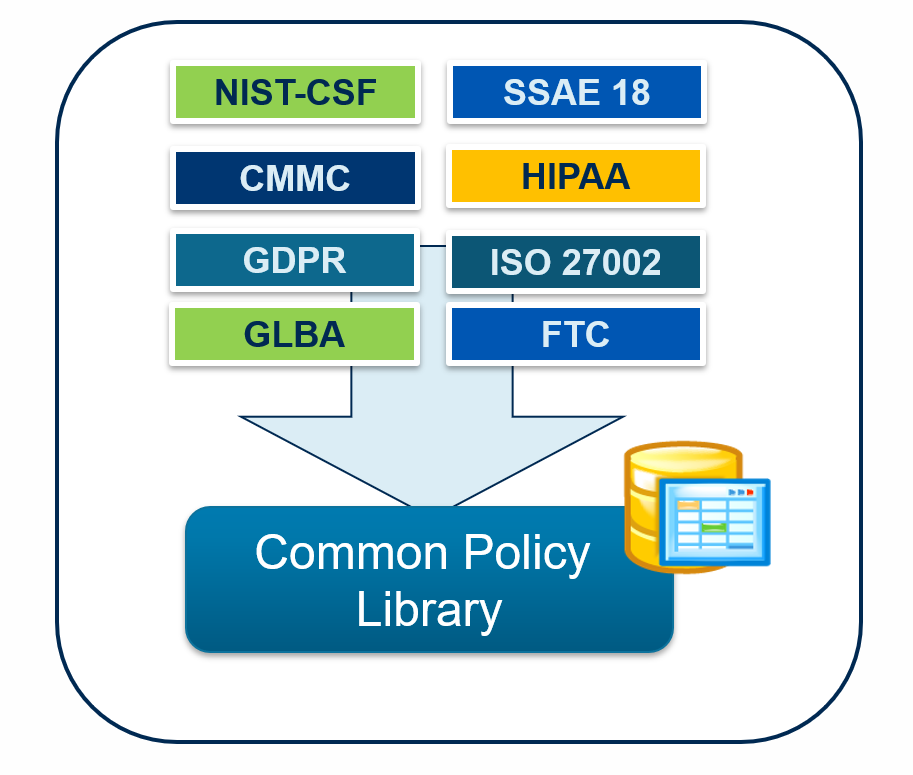
Your organization cannot declare “compliance” with any major cyber framework without a robust set of written information security policies. If your organization does not fall under regulatory requirements, it must have written policies to declare that the organization is following “best practices” for cyber security.
At Information Shield we using the Common Policy Library. This approach leverages mappings from various frameworks into a single common set of controls.
If you need to comply with any of these major cyber frameworks, our Common Policy Library can save thousands of dollars and weeks of effort
