Risk Assessment Policy, Security Policy Whitepapers
Ultimate Guide to Cyber Risk Assessment: Tips & Tools (2025)
Introduction to Cyber Risk Assessment
In our hyper-connected world, businesses face countless digital threats every day. Whether it’s phishing emails, malware, or ransomware attacks, no organization is immune. That’s why cyber risk assessment has become a fundamental part of modern cybersecurity strategies. It helps identify potential vulnerabilities, evaluate the risks they pose, and prioritize actions to protect sensitive data and systems.
Cyber risk assessment isn’t just for large enterprises. Small and medium businesses, non-profits, and even schools benefit from assessing their cyber vulnerabilities. A robust cyber risk assessment can mean the difference between preventing an attack and suffering a devastating data breach.

Key Objectives of Cyber Risk Assessment
The main goals of conducting a cyber risk assessment include:
- Identifying vulnerabilities: Unpatched software, weak passwords, and misconfigured firewalls are all potential entry points for cybercriminals.
- Minimizing financial and reputational damage: Understanding your risk helps prevent costly breaches.
- Ensuring business continuity: A proactive approach ensures that critical operations are not disrupted.
- Meeting compliance standards: Risk assessments help businesses meet legal and industry-specific cybersecurity regulations.
Compliance and Regulatory Considerations
Cyber risk assessments are often mandatory under various laws and standards:
| Regulation or Framework | Requirement |
| FTC Safeguards | Must assess private data breach risks and mitigate threats. |
| HIPAA | Risk analysis is required for selecting controls to protect electronic health records (ePHI). |
| PCI-DSS | Payment processors must assess and reduce cyber risks of systems and third party vendors |
| NIST CSF | Requires all organizations to identify and prioritize cyber risks |
Neglecting risk assessments can lead to data breaches, hefty fines and loss of trust. Even if you have an incident, performing a Risk Assessment can demonstrate due-care and reduce overall liability.
Types of Cyber Risks to Evaluate
Not all cyber threats are created equal. During a cyber risk assessment, it’s important to categorize and evaluate various risk types:
- Malware and Ransomware: Harmful software that can encrypt data or steal information.
- Phishing and Social Engineering: Manipulative tactics that trick employees into giving away sensitive data.
- Insider Threats: Disgruntled employees or contractors with access to systems pose unique challenges.
- Cloud Security Risks: Poorly secured cloud environments can expose business-critical data.
- Third-Party Risks: Vendors and partners can introduce risks into your IT ecosystem.
Part of an effective Cyber Risk Assessment is to score, rank and prioritize risks.
Components of a Cyber Risk Assessment Framework
To thoroughly evaluate cyber risks, organizations typically follow a structured framework that includes:
- Asset Identification: Recognizing all digital and physical assets including servers, applications, and user devices.
- Threat Modeling: Identifying what could go wrong (e.g., malware infection, data breach).
- Vulnerability Analysis: Discovering weaknesses in your current systems.
- Risk Determination: Assessing the likelihood and potential impact of each threat exploiting a vulnerability.
- Reporting: Documenting findings and outlining necessary remediation efforts.
The Risk Assessment Wizard of ComplianceShield automates this entire process.
Cyber Risk Assessment Methodologies
Several trusted frameworks exist to guide cyber risk assessments:
- NIST Risk Management Framework: Focuses on security controls and continuous monitoring.
- OCTAVE (Operationally Critical Threat, Asset, and Vulnerability Evaluation): Ideal for risk-based decision-making.
- FAIR (Factor Analysis of Information Risk): Quantifies risk in financial terms.
- ISO/IEC 27005: Offers a risk management structure aligned with ISO 27001 compliance.
There is no “Correct” risk management framework. Choosing the right framework depends on your industry, regulatory environment, and specific business needs. At Information Shield we help automate all of these methods within our Risk Management Wizard.
How to Conduct a Cyber Risk Assessment (Step-by-Step)
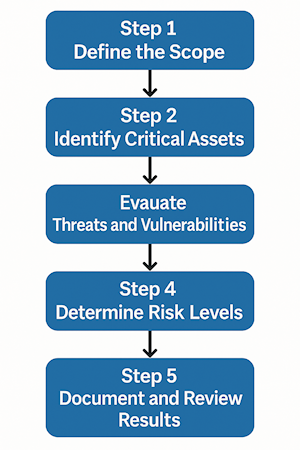
Here’s a simplified breakdown of the process:
Step 1: Define the Scope
Decide what systems, departments, or regions the assessment will cover. If you are just starting, it is best to include the entire enterprise.
Step 2: Identify Critical Assets
List hardware, software, and data that are crucial to operations.
Step 3: Evaluate Threats and Vulnerabilities
Use tools like vulnerability scanners to detect system weaknesses.
Step 4: Determine Risk Levels
Calculate the probability and impact of each threat exploiting a vulnerability.
Step 5: Document and Review Results
Create a risk register and review it regularly with key stakeholders. Automated tools like ComplianceShield provide a built-in risk register that us updated by experts.
Risk Scoring and Prioritization Techniques
Effective risk prioritization ensures that you tackle the most dangerous threats first. Common methods include:
- Risk Matrix Models: Score based on likelihood and impact.
- Heat Maps: Visualize risk intensity across systems.
- Risk Appetite Thresholds: Set acceptable levels of risk.
These techniques allow organizations to allocate resources where they’re needed most. All of these can work together to both prioritize and visualize risk.
Integrating Cyber Risk Assessment with Cybersecurity Strategy
Risk assessments shouldn’t be isolated. They should:
- Feed into your incident response plan.
- Guide patch management and system updates.
- Shape your employee training programs.
- Support ongoing monitoring and testing.
When assessments inform broader strategy, you strengthen your overall security posture.
Cyber Risk Mitigation and Treatment Plans
There are four basic ways to treat cyber risk:
- Accept the risk: For low-impact or low-likelihood threats.
- Avoid the risk: Change processes to eliminate the threat.
- Mitigate the risk: Implement controls to reduce it.
- Transfer the risk: Use insurance or third-party services.
Combining these tactics builds a resilient defense. These options are available automatically in risk management tools like ComplianceShield.

Challenges in Cyber Risk Assessment
Despite its importance, conducting a cyber risk assessment isn’t always easy:
- Constantly evolving threats: Attack vectors change rapidly.
- Resource constraints: Many organizations lack time or skilled personnel.
- Human error: Oversights can compromise the entire assessment.
We build the Risk Assessment Wizard in ComplianceShield to directly address these challenges. No need to spend thousands on a cyber expert. 40 years of experience is built into the software.
Benefits of Regular Cyber Risk Assessments
Conducting regular assessments delivers measurable advantages:
- Enhanced data protection
- Reduced financial losses
- Improved compliance posture
- Increased stakeholder confidence
- Faster breach response times
These benefits far outweigh the investment in time and resources, IF you can perform a real cyber risk assessment with at a cost that works for your organization.
Industry-Specific Use Cases
Here are a few examples of cyber risk assessment for various industries.
Financial Services
Firms have high risk of financial fraud, due to account takeover and other attacks. Detailed risk assessments help identify and prioritize controls to prevent breaches.
Healthcare
Need to safeguard patient data, making HIPAA compliance essential. Risk Assessment is a required control for HIPAA.
Government Agencies
Require risk evaluations for national security and data protection. NIST CSF, CMMC, and NIST 800-50 all require cyber risk assessments.
Small Businesses
Often targeted due to weaker defenses, SMBs risks include data theft and account takeovers due to phishing and fraud.
Future Trends in Cyber Risk Assessment
The future of risk assessment is smarter and more predictive:
- AI-driven risk modeling: Uses behavior analytics to identify threats in real-time.
- Predictive analytics: Anticipates threats before they occur.
- Continuous risk monitoring: Enables 24/7 visibility into vulnerabilities.
Staying ahead means embracing these innovations early. Adopting automated tools can that automatically monitor threats and recommend controls can save thousands of dollars and generate better results.
FAQs About Cyber Risk Assessment
1. What is the primary goal of a cyber risk assessment?
To identify, evaluate, and prioritize potential cyber threats so they can be effectively managed.
2. How often should businesses conduct a cyber risk assessment?
At least annually or after major changes in infrastructure or business operations.
3. Is a cyber risk assessment mandatory?
In many industries, yes—especially where regulations like GDPR, FTC Safeguards or HIPAA apply.
4. What’s the difference between vulnerability assessment and risk assessment?
Vulnerability assessments find flaws; risk assessments evaluate the impact of those flaws.
5. Can small businesses perform cyber risk assessments?
Absolutely. Many free and low-cost tools make it accessible for all business sizes. ComplianceShield offers a very affordable option for any business.
6. What role do employees play in cyber risk?
A huge one—phishing and human error are top causes of data breaches. Cyber Security Awareness Training is key.
Conclusion
Cyber risk assessment is no longer optional—it’s essential. It is required by every major cyber security frameworks and regulation including NIST CSF, HIPAA, GLBA, FTC, CMMC and many more. By identifying threats, assessing vulnerabilities, and developing a strategic plan, businesses can protect themselves from ever-growing cyber dangers. Whether you’re a Fortune 500 company or a local startup, implementing a thorough risk assessment process helps ensure your digital future remains secure.
