Information Security Policy, Security Policy Whitepapers, Writing Security Policies
Information Security Policy: The Complete Guide
Complete Guide to Information Security Policy: Success in policy development and deployment
In today’s digital age, data breaches, cyberattacks, and privacy violations are not just risks—they’re daily headlines. That’s why having a well-structured information security policy isn’t optional anymore; it’s absolutely critical. Whether you’re running a multinational corporation or a small business, the foundation of your cybersecurity strategy must rest on a robust security policy.
Let’s look at what makes a successful information security policy, explore the essential elements, and provide real-world guidance for creating one that protects your business in the future.
What is an Information Security Policy?

An information security policy is a formal document that defines how an organization protects its information assets and IT systems. It outlines specific business rules for ensuring the confidentiality, integrity, and availability of data—commonly known as the CIA Triad.
This policy acts as a blueprint for managing risk, complying with regulations, and maintaining cyber governance. It also acts as a form of “contract” between management, personnel and third-parties such as vendors, insurance providers and regulators.
An information security policy contains high-level business rules. It is different from both standards and procedures, which provide details to support the implementation of security policy.
Why Every Organization Needs an Information Security Policy
Information security policies provide the formal documentation of your cyber security program. Policies provide these essential elements:
- Risk Mitigation – Identify and reduce the likelihood and impact threats before they become breaches.
- Data Protection – Protect the Confidentiality, Integrity and Availability of information throughout the information lifecycle.
- Compliance – Meet the requirements of data protection laws and industry standards (ISO 27002, GDPR, HIPAA, PCI-DSS).
- Operational Consistency – Ensure uniform cyber practices across teams and departments.
- Incident Readiness – Prepare your team to respond quickly and effectively to cyber incidents.
- Trust and Reputation – Build confidence with clients, investors, and partners by having a robust cyber security program.
Key Elements of an Information Security Policy
A comprehensive information security policy typically includes:
| Element | Description |
|---|---|
| Purpose & Scope | Defines what the policy covers and why it exists |
| Roles & Responsibilities | Clarifies who is responsible for policy enforcement and adherence |
| Security Policy Statements | Specific security policy statements, organized by category |
| Policy Enforcement | A statement that describes consequences for non-compliance. |
| Definitions | Definitions of key cyber security terms used in the organization |
| Governance & Review | Listing of Policy Author and approving Senior Manager. Includes update history. |
If you use pre-written security policy templates, make sure they contain these key areas. For example, the Common Policy Library from Information Shield has pre-built templates with each of these areas defined and filled out.
The Five Key Steps for Developing a Security Policy
To build security policies that work in your organization, follow these key steps:
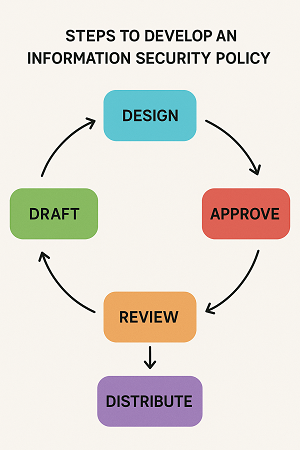
- Design – Pick a Control Framework such as ISO 27001 or NIST CSF to determine your security domains
- Draft – Create a policy document for each Domain
- Review – Review the Document with Stakeholders
- Approve – Get formal approval from Stakeholders, at the minimum some Executive
- Distribute – Once policy documents are formally approved, distribute the policies to each User Group that must read each policy
To facilitate this process, you can use a Policy Automation Tool that provides for these critical steps.
Examples of Common Information Security Policies
The best way to start designing and building a set of security policies is to refence a “cyber security framework”. Examples of common Frameworks include ISO 27002 and NIST CSF. Each of these frameworks define a core set of security requirements that must be met.
To save time and get started on the right foot, consider using pre-written security policy templates like those from SANS or Information Shield. The Common Policy Library includes sample templates for each of these areas and more.
| Security Domain | Description | Sample Policy |
|---|---|---|
| Asset Management | Rules for acquiring, securing and managing IT assets | Asset Management Policy |
| Personnel Security | Rules for secure hiring, management and employment termination | Personnel Security Policy |
| Risk Management | Rules for assessing, ranking and mitigating cyber risks. | Risk Management Policy |
| Data Management | Rules for the collection, and protection of data at rest and during transit. | Information Management Policy |
| Network Security | Rules for Firewalls, Intrusion Detection Systems (IDS) Virtual Private Networks (VPNs) Network segmentation | Network Security Policy |
| Business Continuity and Disaster Recovery | Backup schedules Recovery Time Objectives (RTO) Recovery Point Objectives (RPO) Disaster recovery drills | Business Continuity Policy |
| Third-Party and Vendor Risk Management | Due diligence requirements Contractual security clauses Regular audits of vendor practices | Third-Party Risk Management Policy |
| Data Classification and Handling Procedures | Segment data into categories: Public Internal Use Only Confidential Restricted | Information Classification Policy |
| Incident Response and Breach Notification | Detection Containment Eradication Recovery Communication (internal/external) | Incident Response Policy |
| Access Control and User Management | Define access privileges, password policies, multi-factor authentication, and role-based access control. This prevents unauthorized access and limits insider threats. | Access Control Policy Account Management Policy |
| Acceptable Use Policy (AUP) | Describe acceptable behavior regarding: Internet use Email and social media Device management Data sharing | Acceptable Use of Assets Policy |
Common Mistakes to Avoid in Security Policy Implementation
Even the best-written policies can fail if common pitfalls aren’t avoided. Here are key mistake to avoid:
- Lack of Executive Buy-In
Without leadership support, policies are rarely enforced properly. - One-Size-Fits-All Templates
Generic policies may not address your unique organizational risks. - Overly Technical or Legal Language
Make it readable for non-technical staff—avoid jargon. - Poor Training and Awareness
If employees don’t know the policy exists, it’s like it doesn’t. - Failure to Update Regularly
Outdated policies can create compliance and security gaps.
What to do after you develop an information security policy
After written policies are developed, take the following steps:
- Review Policy Drafts with Key Stakeholders
- Get Formal Executive Buy In
- Distribute security policies to key audiences: Users, Management, Third-Parties
- Train Employees on key policy principles
- Require formal acknowledgement of Acceptable Use Policy
FAQs About Information Security Policy
Q1: Who should write an information security policy?
A multidisciplinary team including IT, legal, HR, and compliance should collaborate. Final approval typically lies with senior leadership or a CISO.
Q2: How often should a security policy be updated?
At least once a year or whenever there is a major change in infrastructure, law, or business process.
Q3: Is an information security policy legally binding?
It can be, especially if referenced in employment contracts or vendor agreements. It also supports compliance with laws like GDPR or HIPAA.
Q4: What’s the difference between an information security policy and a privacy policy?
An information security policy governs data protection internally. A privacy policy outlines how customer data is handled and shared externally.
Q5: Can small businesses use the same policies as large enterprises?
Not effectively. Small businesses need simplified, relevant policies that reflect their unique risks and resource limitations.
Q6: What should be the first step in creating a policy?
Conduct a risk assessment to identify key threats and vulnerabilities. Then, define the policy’s objectives based on that.
Conclusion: Building a Security-First Culture
Creating an information security policy isn’t just about documentation—it’s about building a culture that values digital trust, accountability, and proactive risk management. As cyber threats continue to evolve, your policy must evolve too. Stay informed, involve the right stakeholders, and make your security policy a living, breathing part of your organization’s everyday operations.
The most secure organizations in 2025 won’t just have great technical tools—they’ll have great policies backed by management and understood by employees.
